SHA 256 Algorithm Explained by a Cyber Security Consultant
New malicious programs are coming out every day. The AV Test Institute reports “more than 450,000 new malicious programs (malware) and potentially unwanted applications (PUA)” each day. Due to increased malware activity online in recent years, it’s crucial to protect your data at all times. The SHA 256 algorithm is a powerful tool in your security toolbox that helps to ensure data integrity and authentication.
To better understand this hashing function, let’s explore the SHA 256 algorithm more in depth.
What Is the SHA 256 Algorithm?
SHA-256, which stands for secure hash algorithm 256, is a cryptographic hashing algorithm (or function) that’s used for message, file, and data integrity verification. It’s part of the SHA-2 family of hash functions and uses a 256-bit key to take a piece of data and convert it into a new, unrecognizable data string of a fixed length. This string of random characters and numbers, called a hash value, is also 256 bits in size.
SHA 256 is the industry standard used by the U.S. federal government and many other organizations globally. But what does it do in a more basic sense?
Let’s consider the following example. Say you write the message “Good morning” and apply a SHA-256 hash function to it. It will look like this: 90a90a48e23dcc51ad4a821a301e3440ffeb5e986bd69d7bf347a2ba2da23bd3, Now, say you decide to do the same with a similar message, “Good morning!” It will result in an entirely different string of hexadecimal characters of the same length.
The following graphic shows the SHA-256 hash values of two texts that differ by one character:
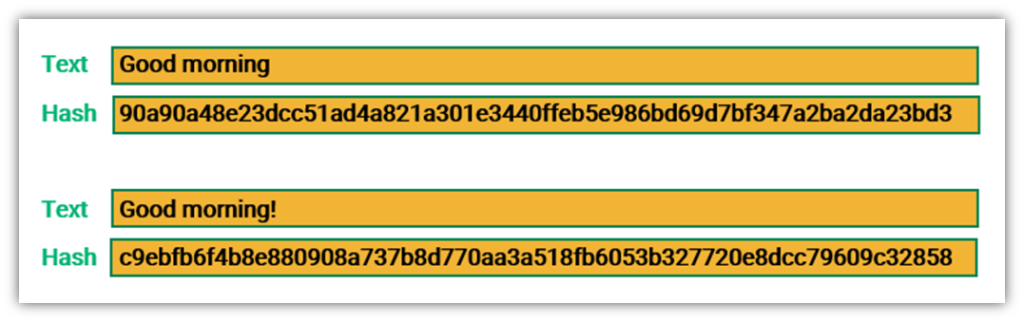
As you can see, when just one character is added to the message, the hash value changes completely. The number of characters in the hash values remains the same, regardless of the number of characters in the original text. This helps to hide the size of the original input data because no matter how big or small the input — a single word or an entire book — it will result in a hash value of the same length.
Now, say you want to send the “Good morning” message to a friend but are worried someone may try to change the message before it reaches your friend. If you provide your friend with the hash value and specify the algorithm you used to create it, then your friend can generate the hash on their end and see whether it matches. If it matches, then they’ll know that your message is authentic and hasn’t been altered since you sent it.
A History of SHA Hashing Algorithms
Secure hash algorithms (SHA) were designed by the National Security Agency (NSA). The U.S. government patented the algorithm, then released it under a royalty-free license so anybody could use it for free. Hashing algorithms are used as one-way functions, meaning that they’re designed to be processed one way but are too cumbersome to reverse engineer.
The SHA-0 algorithm came first in 1993. SHA-1 followed in 1995, and, although it has been cracked, SHA-1 is still in use today. The SHA-2 family, of which SHA 256 is a member, was released in 2001 and includes six hash functions:
- SHA 224
- SHA 256
- SHA 384
- SHA 512
- SHA 512/224
- SHA 512/256
Each member of the family contains a set of cryptographic hash algorithms that convert data into a unique hash value. In the case of SHA 256, the hash value is 256 bits (equal to 32 bytes). The six hash functions have different numbers of rounds and use different shift amounts and additive constants (more on that in a moment).
A Quick Guide to SHA 256 Terminology
To properly understand SHA 256, we need to grasp the terms in the above definition. So, here we go:
Rounds
Earlier, we mentioned that one of the differences between the six SHA-2 algorithms is the number of rounds in each. A round is a set of functions repeatedly carried out in the algorithm to scramble the data beyond recognition. There are 64 rounds in SHA 256 algorithm.
Shift Amount
The shift amount is a fixed method used to shuffle bits. In SHA 256, the blocks are divided into eight segments that are 32 bits each. These eight pieces are then shifted in a specific way that scrambles and randomizes the data.
Additive Constants
The values added to the blocks are called additive constants. In SHA 256, there are 64 constants used to add to the blocks. These numbers are the cube roots of the first 64 prime numbers. This step uses the first 32 bits of the fractional numbers. Those 64 constants are as follows:
| 428a2f98 | 71374491 | b5c0fbcf | e9b5dba5 | 3956c25b | 59f111f1 | 923f82a4 | ab1c5ed5 |
| d807aa98 | 12835b01 | 243185be | 550c7dc3 | 72be5d74 | 80deb1fe | 9bdc06a7 | c19bf174 |
| e49b69c1 | efbe4786 | 0fc19dc6 | 240ca1cc | 2de92c6f | 4a7484aa | 5cb0a9dc | 76F988da |
| 983e5152 | a831c66d | b00327c8 | bf597fc7 | c6e00bf3 | d5a79147 | 06ca6351 | 14292967 |
| 27b70a85 | 2e1b2138 | 4d2c6dfc | 53380d13 | 650a7354 | 766a0abb | 81c2c92e | 92722c85 |
| a2bfe8a1 | a81a664b | c24b8b70 | c76c51a3 | d192e819 | d6990624 | f40e3585 | 106aa070 |
| 19a4c116 | 1e376c08 | 2748774c | 34b0bcb5 | 391c0cb3 | 4ed8aa4a | 5b9cca4f | 682e6ff3 |
| 748f82ee | 78a5636f | 84c87814 | 8cc70208 | 90befffa | a4506ceb | bef9a3f7 | c67178f2 |
Where Is SHA 256 Used?
We can use SHA 256 in situations where we need the following:
Protecting the Data Integrity
When we communicate online, we assume that the reply is coming from the person we think it is. How true is that assumption? Well, if the communication is not sufficiently encrypted, a cybercriminal can easily intercept it and pretend to be the other party.
SHA 256 ensures data integrity so that both parties can be sure that the communication is actually from the person they think it is. The recipient device creates a hash of the original message and compares it to the hash value sent by the sender. If both hash values are equal, the message has not been tampered with during transit.
Verifying Digital Signatures
A digital signature is a way of signing digital documents, code, or software that’s verifiable by the recipient or users. This way, they know whether you created or signed the document or file, or if the item in question was created or altered by someone else.
A digital signature is created by applying a hash to the file and then using an encryption algorithm to encrypt it via private and public keys. The private key is used when the signature owner signs the document; the public key is used by the recipient to decrypt the message on their end.
But all of that would mean nothing without verification, which is where SHA-256 comes in. Hashing ensures that the digital signature hasn’t been altered since it was signed. The recipient’s system runs the hashing algorithm on its end and uses the public key to decrypt the message. If it matches, then it knows the data is unaltered and authentic.
Verifying Blockchain Transactions
It may surprise you to know that SHA-256 is also used in some popular blockchain applications, most notably the cryptocurrency Bitcoin. Block headers are integral to blockchains, as they help to “chain” one block of transactions to the next in a specific order. SHA-256 hash helps ensure that no previous blocks are changed without altering the new block’s header.
Examples of Where You’ll Find SHA 256 in Use
SHA 256 is one of the most reliable algorithms for authentication and message integrity verification. It’s used with many different authentication and encryption protocols and processes, including:
- SSL/TLS — Secure socket layer (SSL) and transport layer security (TLS) are encryption protocols that maintain data integrity and confidentiality while it’s in transit.
- SSH — Secure Shell (SSH) protocol creates a secure channel between two devices for data transfer.
- IPsec — Internet protocol security (IPsec) is a collection of protocols designed to secure data transfer across different IP networks.
- PGP — Pretty good privacy (PGP) is an encryption algorithm used to sign, encrypt, and decrypt emails, files, directories, or a disk partition.
- S/MIME — Secure/multipurpose internet mail extensions (S/MIME) is an algorithm to secure the integrity and confidentiality of emails.
- Blockchain — In a blockchain, preceding hash values are used to calculate the hash value of the current block.
Is SHA 256 Secure?
Is it possible to crack the SHA 256 algorithm? Sure, if you have virtually unlimited resources and time. But in reality, no, nobody has so far. That’s why the Bitcoin network, regarded as one of the most secure networks globally, uses SHA 256. That’s also why TLS certificates use SHA 256 to validate their integrity. The following screenshot shows the TLS certificate of our website:
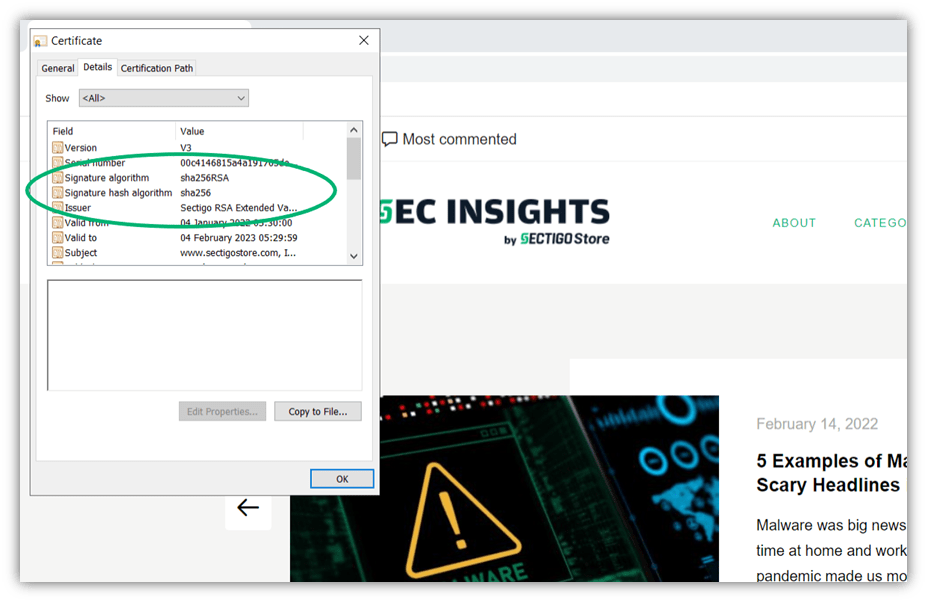
When you use the SHA 256 standard in an algorithm, you can get it verified using the Cryptographic Module Validation Program (CMCP) from the National Institute of Standards and Technology (NIST) and the Communication Security Establishment (CSE). By law, certain U.S. government applications are required to have this official verification.
How Does the SHA 256 Algorithm Work?
SHA 256 is very complex, so we’re not going to go into too much detail here. However, we can understand it from a broad perspective. FIPS-180 describes SHA algorithms as involving two essential stages:
- Preprocessing — This is where the message is padded, broken down into smaller blocks, and initialization values are set.
- Hash computation — This process involves a series of operations that result in a series of hash values. The 256-bit resulting hash digest we get at the very end is generated by computing these various hash values.
SHA 256 follows the steps given below:
- First, data is converted into binary. Binary code uses 0s and 1s to store information. For example, the letter ‘a’ is written as ‘01000001’ in this basic computer language.
- The binary data is divided into blocks of 512 bits. If the block is smaller than 512, it’ll be expanded to that size by adding bits of “padding.” If it’s larger, it’ll be broken into blocks of 512 bits. (If the last block isn’t exactly 512 bits, padding is added to the last block to make it 512 bits.)
- The message is further divided into smaller blocks that are 32 bits each.
- Sixty-four iterations (rounds) of compression functions are performed, wherein the hash values generated above are rotated in a specific pattern and additional data gets added.
- New hash values are created from the output of the previous operations.
- In the last round, one final 256-bit hash value is produced — this hash digest is the end product.
Final Thoughts on SHA 256 Algorithm
Even though we didn’t get into the nitty-gritty of how the SHA 256 algorithm works in this article, you should now understand that SHA 256 is a very useful function. SHA 256 converts data into fixed-length, virtually irreversible hash values, and is mainly used to verify the authenticity data.
As we mentioned earlier, no one has been able to crack SHA 256 to date, and it’s used in some of the most secure networks in the world. One day, SHA 256 might break, but for the moment, we can rely on it to keep our data safe.










No comments:
maheshcyberadvisor@gmail.com